Web server and website maintenance best practices
General requirements for website and server maintenance
Zsolt Lengyel
There are many website hosting companies on the market. Sometimes, the hosting provider will also provide an easy-to-use web interface that can be operated with minimal technical knowledge.
Once a website is well set up on these platforms, it can be up and running for a long time with low traffic. However, the server hosting the website will need maintenance from time to time, as will the source code (engine) of the website, or even its content.
If maximum uptime is important and you want your website to be secure, then you should invest more in the design of the server environment, and its maintenance is highly recommended.
What technologies should you choose? What to look out for? What are the general needs of a website and what are the pitfalls of hosting in the long term?
Backups
A backup is essentially a snapshot of the entire state of your website at a given point in time.
If you want to restore your website to a previous state for some problem or other reason, such as accidentally deleting content or making an incorrect setting, restoring from backup is probably the way to go.
With hosting providers, backup is often included in the package. However, restoring them is usually a task that requires a specialist (it is less common for the web interface to enable the user to accomplish this with a few clicks), so it is important to have help from the provider to do the restore. It's good to know that although backups are usually part of the hosting service, restoring them often comes at an extra cost.
It also makes a difference how far back the backup is stored. For a frequently visited and monitored website, 1 per day, roughly 1 week back is sufficient.
It is definitely worth testing this feature at least once before committing to a hosting provider.
SSL certificate
Having an SSL certificate is now a basic requirement for a website.
If the website has an SSL certificate, you will see a padlock icon to the left of the web address in the browser, or if you copy the URL from the address bar and paste it into a text file, you will see that it starts with https instead of http (the “s” in this case stands for “secure”).
The degree to which a hosting provider makes it convenient for the customer to request and configure an SSL certificate varies. It may be as simple as one click, but it may also require administrator intervention.
What do you really need an SSL certificate for?
- If you have one, data traffic between the browser and the server will flow over an encrypted channel, which would be quite costly for an attacker to intercept. It's no coincidence that https has been a Google ranking factor since 2014!
- It inspires confidence in the user, even if the website does not have any login function, only displays information. If the website does not have an SSL certificate, the browser's address bar will display “Not secure” in place of the padlock:
Which SSL certificate should you choose?
There are many certificate issuers available and it can be difficult to decide which one is the best. There are free, cheap and expensive certificates, and one may well ask: is the more expensive one better? The answer is: not necessarily.
It all depends on the server configuration. A certificate can be very expensive if the server-side security settings are not right.
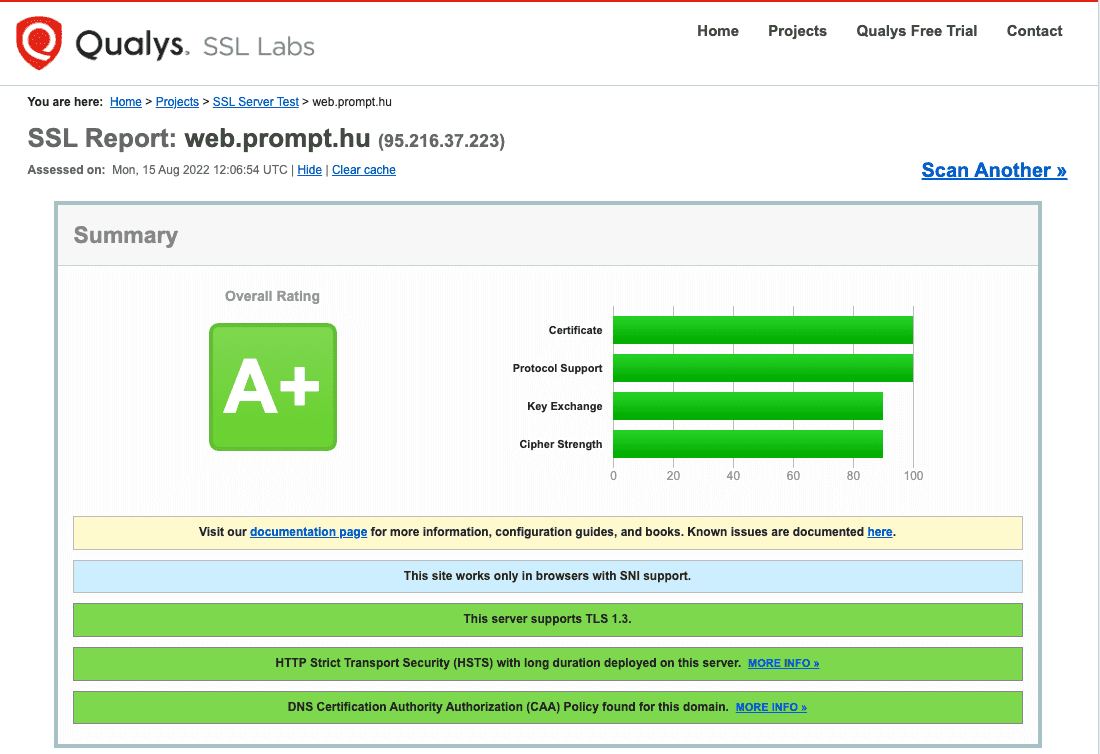
To check the settings, the online SSL server tester available at Ssllabs.com, for example, is quite straightforward. It gives an overall rating of the quality of the SSL certificate.
Web.prompt.hu, for example, gets an A+ security rating using the free Let's Encrypt certificate issuer:
Uptime
The uptime is the time the website is available. The higher it is, the better — and the less downtime, i.e. when the website is unavailable, the better.
Whether it's the website or the server hosting it, there is some downtime from time to time, for example during maintenance. It is best to schedule downtime when the website has minimal traffic. It is also important that downtime lasts for no more than a few seconds.
The only way to check uptime manually is, of course, to visit your website from time to time and see if it is working.
However, online monitors, such as the free UptimeRobot, are more effective, testing website uptime every minute or so and sending an email or even a push notification to your phone if your website is down. This feature might also be configured by the website hosting company, and in case of downtime, they will take immediate action. When the hosting provider doesn't offer this service, the owner can also set it up on their phone and, if they receive a notification, report the downtime to the hosting provider.
Protecting forms and login interfaces
Even on a simple website, it is quite common to see a contact form that, when filled in by a visitor, the website owner receives an email notification and can respond to it.
These forms need to be protected by appropriate technology, so-called CAPTCHA protection, to prevent automated scripts, spamming robots from filling them in and flooding the website owner with unsolicited mail.
This is the responsibility of the website developer, but there are also server-side services that protect such forms or even login interfaces.
The most popular content management system based websites (such as WordPress or Drupal based ones) always have a login area where administrators can log in by entering a username and password.
If an attacker finds this interface, they have an endless opportunity to try to enter a username and password if the website and server are misconfigured, and if they keep trying, they will eventually find a weaker password and gain administrative access to the website.
Such login interfaces are protected by restricting the attempting user by IP address or other identifier, for example after three incorrect passwords, or by blocking the user completely.
This protection is not set up by most hosting providers, so the website is both vulnerable to attack and performance is degraded. This is because during the time that the website is under attack (while the attackers keep trying), the server is busy serving the attacker, leaving less resources for the real visitor (as the server cannot distinguish the attacker from the average visitor).
There is server-side software that can be good protection against such attacks — for example, for a CMS based website with average traffic, properly configured Fail2ban can be perfect. However, setting up such server-side software requires a specialist.
Monitoring
The website is subject to varying degrees of load during its operation. Depending on the type of use, it is worth monitoring the various parameters of the server hosting the website, as well as the uptime of the website.
If, for example, the web storage space is full because too many or too large images or videos are uploaded, the website may stop working. If the processor is overloaded, the server is not able to serve all visitors, which means that for some visitors the website loads, while for some, it does not.
Basic server parameters such as processor utilisation, storage space, memory usage, but also website traffic can all be monitored, even with free server-side software.
At Prompt, we use the free Prometheus data logger and Grafana dashboard to monitor the vital signs of our servers.
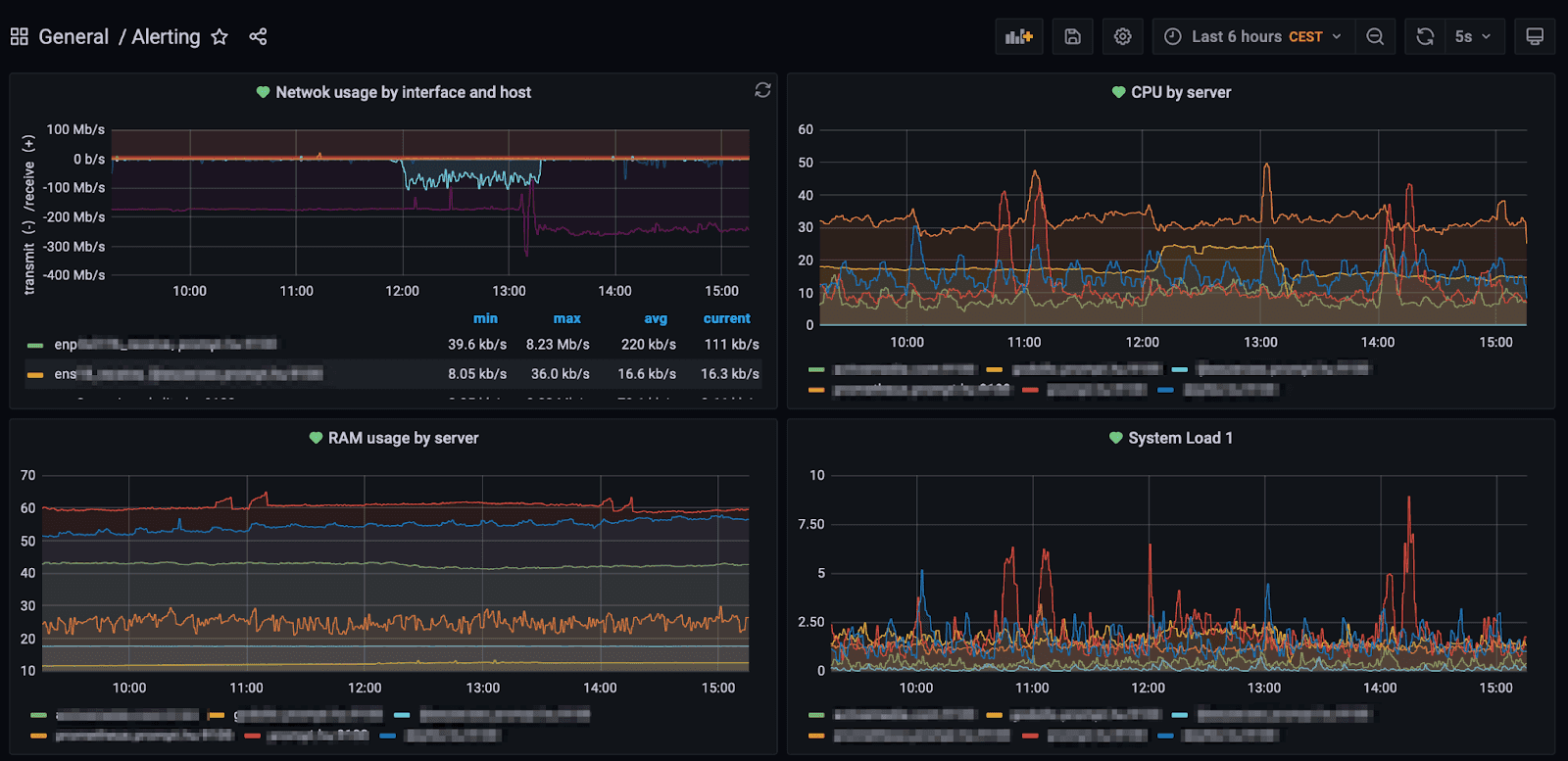
Server monitoring does not mean just setting up a system and then projecting the nice graphs onto a big screen and having someone sit there. It's important to be able to look back at events if you want to track something back. Another important function of the monitoring system is to check the values of various parameters on the server, and if they reach a preset limit within a given time, it sends a notification to the operator.
The installation of such software also requires a specialist, and such monitoring software is now quite rarely available from the average hosting provider. Of course, when they are available, the notifications that the system sends are the responsibility of the hosting provider's internal IT team, and they are the ones responsible for responding to the notifications sent by the monitoring software.
Open ports
The principle of least privilege also applies in a server environment, in the sense that services that are not needed should not be turned on unnecessarily or be available to anyone who does not need them.
In general terms, a port number is a (numbered) “gateway” through which you can communicate with a service running on a server (if it is running, of course).
A web server can (usually) be accessed via TCP port 80 and TCP port 443, which is how the web page you are visiting is displayed in your browser.
When a web page loads in our browser, it means that the server hosting the web page has TCP port 80 (for HTTP) and TCP port 443 (for HTTPS) open. These two ports are necessary for the web server to work normally and serve its visitors.
However, there are ports that allow an administrator to log into the server remotely and make administrative changes or maintenance on the server.
However, the situation where an administrator needs to be able to access the administrative areas of the server from anywhere in the world is quite rare, so ports that allow this (e.g. SSH, RDP, etc.) should be blocked.
Now the question arises: how do we perform administrative maintenance on the server if these ports are closed? The answer is that the ports can be opened from certain IP addresses. For example, an administrator logging in from an IP address at work can access the administration interface on the server, but not from anywhere else in the world. This makes it impossible to attack these services from anywhere in the world through the open port, because the server's firewall will simply drop requests on these ports if they come in from an IP address other than the company's own office.
On Linux servers, you can set up such protection with a firewall called nftables (formerly iptables).
This of course begs the question: how does the administrator maintain the server when he is not in the office? The answer is: using a VPN service.
Virus scans
The source code of the website hosted by the server often contains third-party source code. As a result, websites based on CMSs may contain vulnerabilities that allow an attacker to inject infected code or files into the server.
Consequently, virus scanning is also required on the server to filter out the viral source code or file and quarantine or delete it from the server.
Server-side virus scanners include Amavis and ISPProtect, which is specifically designed to scan websites (and which also uses Amavis in the background).
Such anti-virus software should also be installed and run regularly on the server by a competent professional.
Web application firewall
A web application firewall can be a primary line of defence.
This is a separate piece of software that sits between the web server and the visitor, monitors traffic and if it detects suspicious activity, it blocks the request.
A web application firewall can be installed directly on the server, but you can also use external providers such as Cloudflare.